It’s the new black – working in cafés, patisseries, hotels, airports, train stations and other nice places with free Wifi, where you just have to spend time, voluntarily or against your will.
It’s the new black – working in cafés, patisseries, hotels, airports, train stations and other nice places with free Wifi, where you just have to spend time, voluntarily or against your will. Why waste time while you wait? Email, browse some websites, check Facebook or do your banking.
Wifi networks are leaking like a sinking ship. Your, as well as thousands of others’ public waiting has become a major source of income for cyber criminals. If you thought that your conversation, banking details or pictures with questionable content were safe and secure, it’s time to think again. All common, public, free Wifi networks are open for anyone to listen in to.
For those with the right equipment, it’s like reading an open book, where the pages display your life, your friends and contacts, or perhaps your business secrets. As soon as you are attached to the Wifi network, your data will be available to anyone with the proper equipment.
And it’s not very expensive to do. All one needs is a laptop and some free software.
And you won’t notice. Until afterwards, when your identity has been hijacked, and your contact list, your drawings for the next product or your sensitive e-mails have been taken hostage.
1 Please! No more yapping about IT security!
No more IT security now! The phone keeps getting updates all the time. Don’t the manufacturers keep track of all the threats? The updates are a nuisance when I’m swiping good lookers!
We’re sorry. The attacks are not aimed at the phone itself, but the data being transferred and the information content.
2 It won’t happen to me!
Yes, it will happen to you and in this article we will show how attacks are done and how simple they are.
The Wifi connection is protected by password and WPA2 encryption these days, isn’t it? It is protected with AES encryption! We’re sorry, again. If you walk around the streets of London and investigate, WPA2-protected networks are relatively rare. But the completely unprotected networks are all too easy to intercept, so this article is dedicated to WPA2-protected networks.
No more IT security now! The phone keeps getting updates all the time. Don’t the manufacturers keep track of all the threats?
3 Three-pronged attacks require three-pronged protection
Your personal, secret information may be revealed by attacks on three different layers.
- The wireless network
- The evil apps
- Your own carelessness
There are methods to cope with all three. How, you are about to find out.
4 The big picture
The attack could happen inside the access point, which might be equipped with spyware. Or, an intermediary computer might be connected somewhere on the outgoing line, stealing plain text data before it reaches the Internet. Who equips a router with spyware? It has been discovered that some totalitarian states are very keen on that.
A VPN tunnel from Hidden24 will protect you from all this. The tunnel looks like the green “pipes” in the illustration above. The “tunnel” consists of a cipher made up between you and Hidden24 that cannot be broken into by an outsider. The attacks just bounce off.
However, the VPN tunnel must be removed before your data can be used to access a website. Hidden24 will remove it in a secret location, in an unspecified country, where it cannot be eavesdropped on. Your data is then transferred to the Internet in the unencrypted condition it has to be. It is up to you to choose a harmless website online. The vast majority of websites you visit every day are harmless, at least superficially.
All devices that talk over the Internet must have a so-called IP address, i.e. a fingerprint on the Internet. If the receiving server happens to be a bit shady, it may pass your IP address on to those willing pay for it. Hidden24 hides your IP address and replaces it with another one.
Many wireless networks are “protected” by some form of encryption, which unfortunately does not provide protection against a perpetrator with the right equipment.
5 Layer one – attack on the Wifi
The vast majority of personal computers are already fully equipped for snooping on Wifi networks, without any special hardware additions needed. All you need is a special program, such as CommView for Windows, which is freely available on the Internet, and some technical knowledge.
It all starts with sitting down with your cup of coffee, starting up the snooping computer and CommView. The public password you will get when you pay for the coffee.
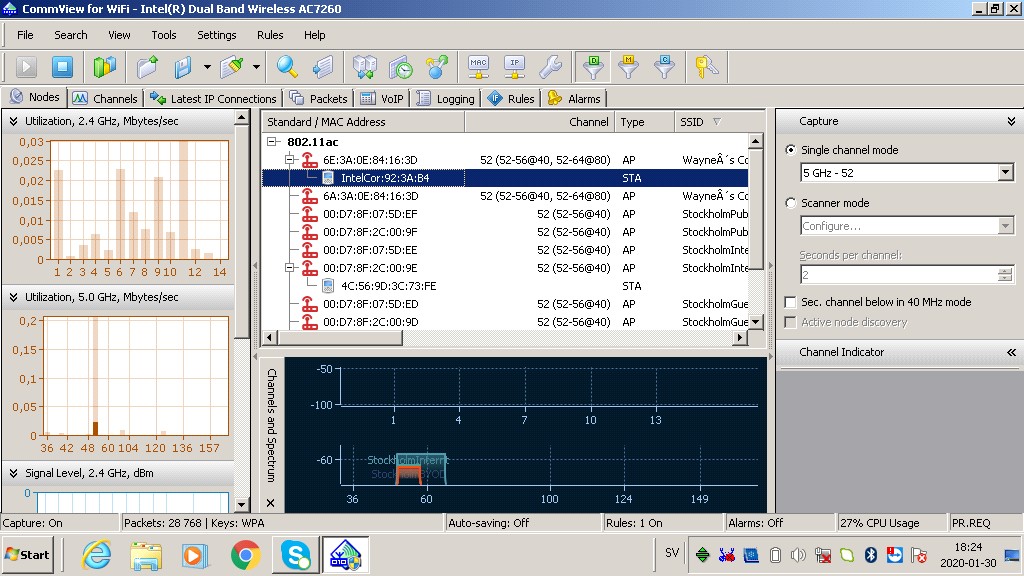
The Nodes tab on the Home screen displays traffic volumes on the 2.4 and 5 GHz bands (left), an overview of the 5 GHz band (bottom center), and all access points within your computer’s range and their MAC addresses (top center). The header bar details the network interface card built into this computer, an Intel AC7260 with MIMO capability.
As you can see, the access point we intend to attack is Wayne’s Coffee on channel 52 on 5 GHz with the MAC address 6E:3A:0E:84:16:3D. The test computer we intend to attack (another machine) is already connected to the AP, and is called “IntelCor” and its MAC address starts with 92:3A:B4… The test computer is not yet logged in. Just wait for it to log in.
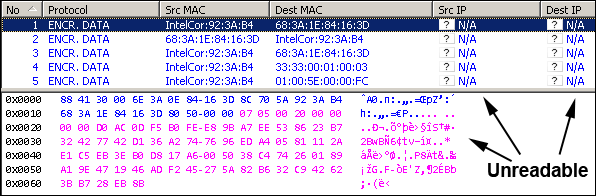
To start snooping, switch to the Packets view, which decodes the captured data packets and displays them in both hex code and transcoded into readable letters.
At first, you can’t read any encrypted traffic at all.
You will recognise the MAC addresses in the conversation because they are always sent unencrypted, whereas the IP addresses involved, source and destination, and data in the data packets, are unreadable (ENCR. DATA).
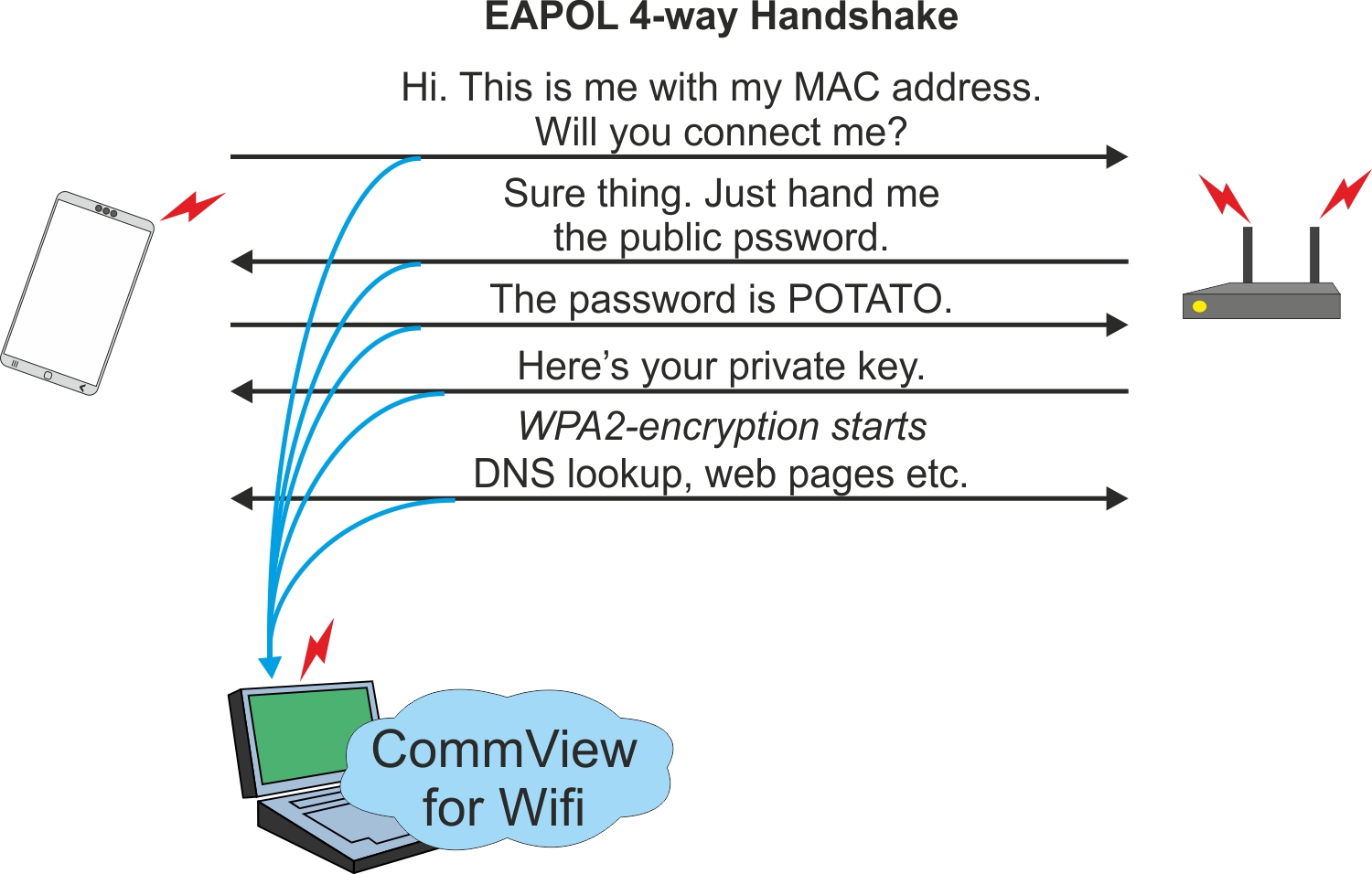
Let’s start the attack. The reason why CommView can read the WPA2-encrypted data is because the program is listening in from the beginning of the authentication sequence and then recreating exactly the same process as the computer requesting a connection, taking the private key handed out by the Access Point and creating the same WPA2 encryption sequence as the computer seeking connection. The connection sequence, when the access point hands out a private key to anyone who wants a connection, is called an EAPOL 4-way Handshake.
Since both stations got hold of the same private key, both can start the exact same encryption sequence, which is the same as encryption not existing for either of them.
6 DNS lookup
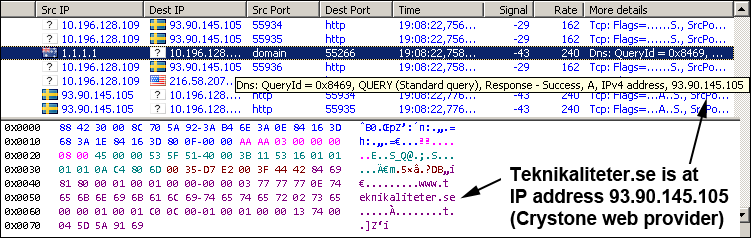
The connection is now revealed. The user wants to browse a website. He starts by entering a URL in the browser, which is sent to a DNS server, asking the server to provide the site’s IP address.
The user is interested in technology and wants to visit the website Teknikaliteter.se and asks the DNS server at address 1.1.1.1 (a server owned by Cloudflare Inc. in Hong Kong) to respond with the IP address. The answer is 93.90.145.105 (which is the web host Crystone owned by Levonline AB in Stockholm). As you can see, the DNS call and response are not encrypted.
7 Arriving at the destination
The home page data arrives from Teknikaliteter.se. CommView stores incoming data in a file on the hard drive.
Incoming HTML code is saved in a file and displayed in a web browser. The actual appearance of the site is displayed on the right and the result we captured is displayed on the left. It was not possible to accurately reproduce the complete graphical layout of the Teknikaliteter.se, but it does not matter as all the crucial information, links, pictures etc are represented. Anyone who wants to capture compromising information should be more than satisfied.
8 What can be attacked?
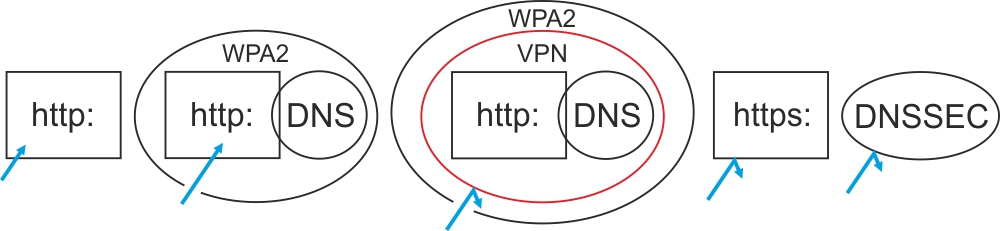
The above five scenarios are common in Wifi traffic and on the Internet. CommView can easily break into unprotected http traffic and apparently has no problem breaking through WEP, WPA and WPA2 traffic. On the contrary, a VPN tunnel from Hidden24 is impossible to break into. Without knowledge of private keys, it is also not possible to break into https traffic, but these can be obtained (see below). DNS lookups with DNSSEC are encrypted and very difficult to see through.
- The deplorable fact is that unprotected Wifi networks and networks that you believe are protected with WPA2 are actually completely transparent.
- It is equally regrettable that, for example, some English authorities do not use DNSSEC.
9 So, https is impervious?
Not quite. In order to decrypt https, you must have the encryption key from the web server holding the website. It can be obtained by, for example, breaking into the server and stealing the certificate, or by infiltrating the organization and buying or negotiating to get the key.
Note that the DNS call to the https-protected server is still open, so one can still see which web address (URL) you are using. It can be quite dangerous for a dissident from a totalitarian country, or someone who has moved to England and is being threatened by refugee espionage.
10 Fake networks and intermediate attacks
Snooping on radio traffic is just one of the ways to attack public Wifi networks. When connecting to a free of charge network, it is up to you to make sure that you are actually connecting to the right provider. You put a lot of trust in a network name.
Probably your local café is not very villainous or looking to steal your sensitive corporate data, but it is very easy to set up a fake network with a similar name and steal the connection from someone who is in a bit of a hurry or not so careful. Especially if the list of available networks is very long.
The deplorable fact is that unprotected Wifi networks and networks that you believe are protected with WPA2 are actually completely transparent.
Just connect to a fake network and lo and behold, the https encryption doesn’t matter. Once a computer or phone is connected to a fake network, the connection can be manipulated using a man-in-the-middle attack. The most common method is to forward your connection to a counterfeit version of the site you were looking for. The fake website has only one thing in mind, to grab your personal information, account number, credit card number and so on. Once you have provided all your valuable information, you will be redirected to the genuine site, without having noticed.
In that case, a VPN can’t help you. The only thing that happens is that you get a completely secure VPN tunnel to the fake service. You must make sure not to get lost among the available networks and services.
11 Layer two – the evil apps

A VPN protects you from snooping computers in a café, but it will not shield against shady apps installed on the phone, that will send your data to interested buyers on the Internet, such as advertising companies and totalitarian governments.
The spy apps running on your phone or computer will have access to the clear text and images stored in memory, or whatever you type on the keyboard, before it is encrypted by the VPN app and becomes unreadable to the outside world and sent along inside the VPN tunnel.
So the spy apps can freely have their share of everything on the phone. Since they are not visible and thus not “exist”, you can also not block their access to various types of data. You may have the location service turned off because you do not want to reveal your GPS location to anyone. The spy apps don’t have to bother with that. They manage their communication with your GPS receiver and their evil remote server discreetly, so you don’t see it.
How did the spy apps get into the phone to begin with? On the one hand, the telephone manufacturer could have installed them during manufacture and have them hidden so that they are not visible. Or they are among those visible, pre-installed apps that cannot be deleted (bloatware). Or they may be popular apps that you downloaded yourself because they seemed exciting, or did something fun, such as distorting a face, providing various image filters, pretending to encrypt your calls, or whatever.
12 Layer three – attacks against better judgment
There will always be emails about loans that you have not asked for, competitions that you won even though you did not participate, and a rich widow in Nigeria who wants to give you fictitious money, all nicely designed for you to click on them.
A VPN protects you from snooping computers in a café, but it will not shield against shady apps installed on the phone, that will send your data to interested buyers on the Internet, such as advertising companies and totalitarian governments.
A nice collection.
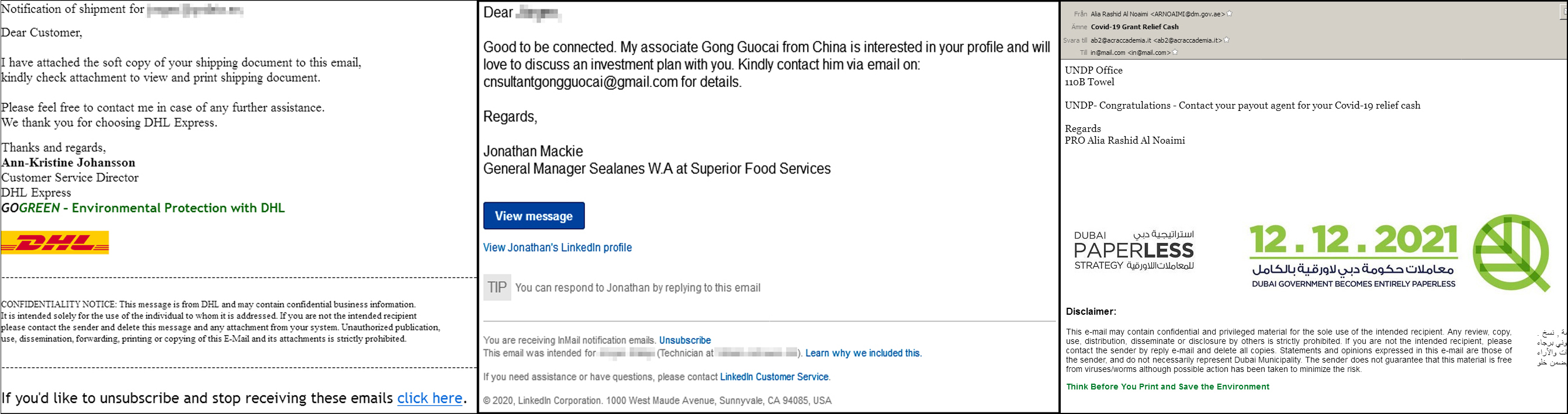
No, I haven’t ordered any package to be delivered through DHL. Perhaps someone else did, in my name? By mistake? The email has the DHL logo and looks alright. It just isn’t. Do you actually know a Mr. Ding Dong from China who might be interested in discussing an investment plan with you? Probably not. Delete it. Did you ask for Covid-19 relief money from Dubai? From a bank living in a Towel? Although the mail has all the logos and everything, you better forget it.
If you participate in an online survey, you are guaranteed to be overrun by advertising afterwards. If you click Unregister, the sender will know that you exist and continue to send you stupid emails. There is only one button to click: Delete. Send to trash. Empty the junk folder every day.
Someone may offer you great terms, but think for a moment about which country, for example, has the .pw top-level domain? It’s Palau. An archipelago in the Pacific. Do you have any business relations in Palau? Shouldn’t think so.
Or why not an email from the good old Post Office, in Hungarian? With a link you shouldn’t click on.
There are no electronic safeguards in the world that will protect against this sort of nonsense.
13 This is even simpler
14 What will you do about it?
The important thing is that you should be aware of the risks of the Internet.
- Get a VPN from Hidden24 and always activate it when surfing in public places, on airplanes, on trains, in hotels and in foreign countries.
- Be cautious when surfing the net in public and consider what information may be sensitive and how to handle it.
- Don’t download all the apps in the app store just because they seem exciting or friends recommended them. First, check if they are safe.
- Even supposedly secure services, such as social media, have proven to be unsafe, as they sell your personal information, opinions and preferences to advertising companies or companies that work to influence general elections.
- If an offer seems too good to be true, it probably is. Nobody wants to give you millions.
15 The FBI recommends
The US Federal Bureau of Investigation recommends avoiding public Wifi networks at airports, hotels and other places that offer free Wifi. If you absolutely have to use these networks, you should follow the steps the recommended by the network provider to connect, to avoid fake networks. However, the best thing is to use a VPN service.
There is a war going on in your Internet connection. There is no sound, there is no smoke, but the war is on all the same.
16 Read more
FBI recommends using a VPN for public Wifi: https://www.youtube.com/watch?v=bzD6paYozGI
The US Federal Bureau of Investigation recommends avoiding public Wifi networks at airports, hotels and other places that offer free Wifi.
MORE ARTICLES TO READ

Privacy
Integrity – Nag, Nag, Nag!
The problem with integrity is that it is a bit abstract and difficult to grasp as a con...

Hacks and Incidents
The Big Hacks that Shook the World
Hackers are international criminals. The Internet allows them to operate anywhere in th...
Hacks and Incidents
How to recognise phishing email
Do you think all the exciting emails that land in your inbox came from your friends or ...

Privacy
How to be invisible online
The Hidden24 essential guide to staying on the grid, but less visible The Hidden24 esse...

VPN
Hidden24 top 10 rated in Tech Advisors VPN review
Hidden 24 has been ranked in the top 10 VPN providers, out of 100’s reviewed by IDG’s T...

VPN
VPN: The Ultimate Beginners Guide
VPNs are quite popular with everyone in today’s world. VPNs are quite popular with ever...